Identity at Golem
Why does Golem want to build a reputation system?
The Golem Network recognizes the importance of security, and that is why we are in the process of researching identity management options. We believe that to attract more requestors and enable further use cases, the network might need to include mechanisms to increase trust between its users.
Blockers from the user side
From a user perspective, trust is a major concern on the Golem Network. While, in some cases, it is perfectly acceptable to have fully anonymous actors in a decentralized network, in certain scenarios, we are thinking about introducing a level of identification to enhance trust for all parties.
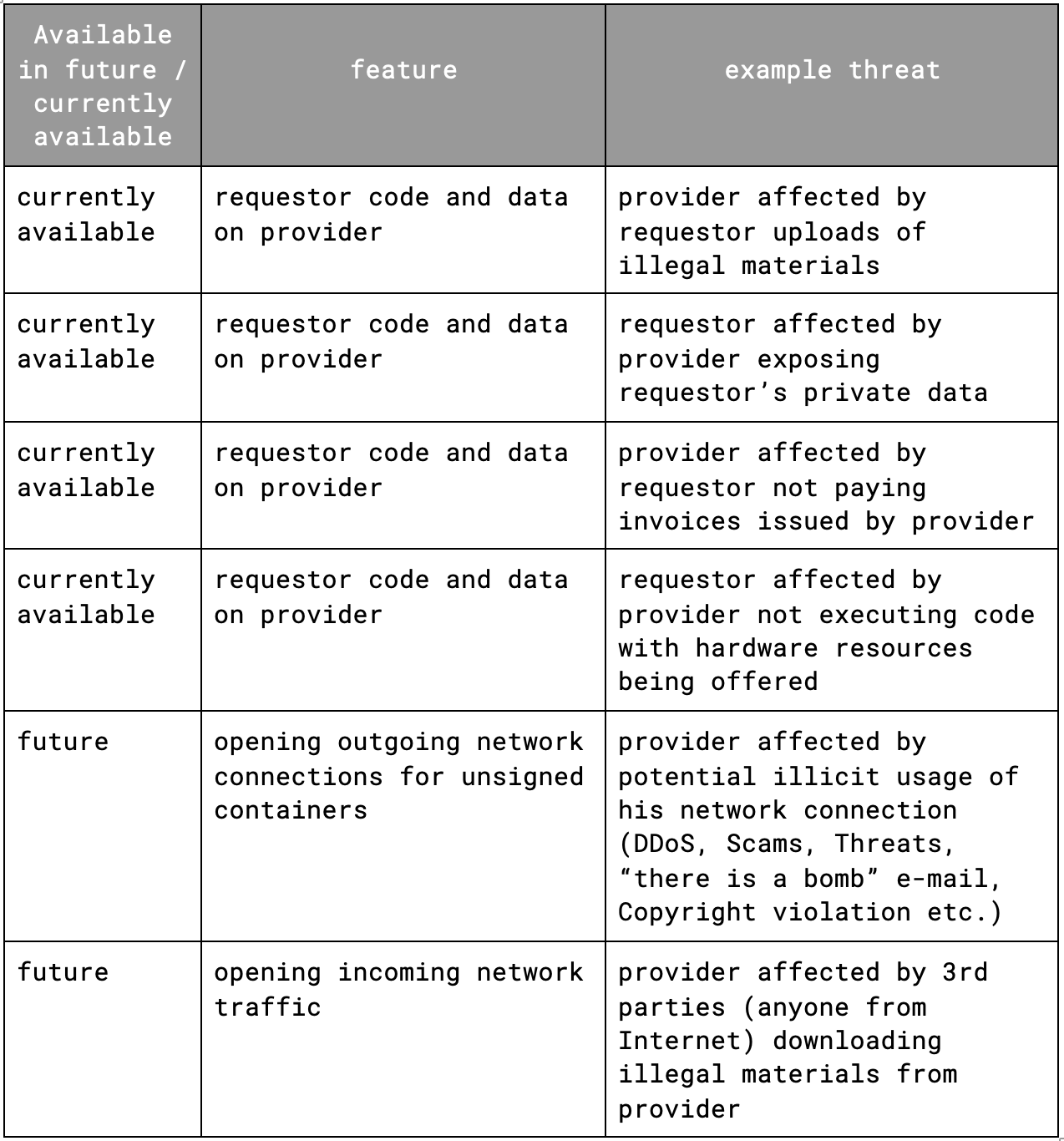
Currently, providers cannot identify requestors using outgoing network traffic on their machines, storing requestors’ data, or executing a requestor's code. In the future, hosting services with open incoming connections or even more open outgoing network traffic will be possible. Requestors may also be hesitant to upload their personal data and run their code on untrusted hardware. Why? Because they cannot always be sure they will receive reliable results and that their sensitive data will not be compromised. Providers could also be concerned about not being paid by requestors, processing illegal content, and being used for unwanted activities.
For example, imagine your provider machine participating in a DDoS attack. If the requestor identified themselves with social or full KYC at the outset, perhaps this could be avoided? This is why we are researching identity management options.
Best practice implementations
To address these concerns, Golem is exploring the idea of using an opt-in identity system that encourages providers to offer more trusted computations. Non-anonymous nodes will be less likely to engage in malicious or illegal activities, and creating a new identity and gaining a reputation will be more difficult.
Gathering feedback
To gather feedback from the community, we are conducting surveys to understand the types of KYC methods that would make providers more likely to enable certain features like opening outgoing network connections or enabling incoming network traffic. Also, we would like to ask about the level of KYC that would make requestors comfortable uploading sensitive data on providers’ machines and the level of trust that would allow users to execute requestor code or use/build reputation systems. Additionally, we’re asking members of our community whether they have ever been hesitant to run a Golem node due to a lack of information about other users and whether adding identity information could increase their trust in the network.
Implementation
The results gathered during this survey will help us to analyze this challenge and design solutions to ensure the Golem Network better meets the needs of its users.
Would you like to help us and take part in the survey? Click on this link and fill out the form. Thank you.
LINKS:
Survey for the requestor: https://glm.zone/requestorsurvey
Survey for the provider: https://glm.zone/providerssurvey